ClickFix to Linked-Device Takeovers: Will Star Blizzard Introduce a New Initial-Access Vector by Oct 2026?
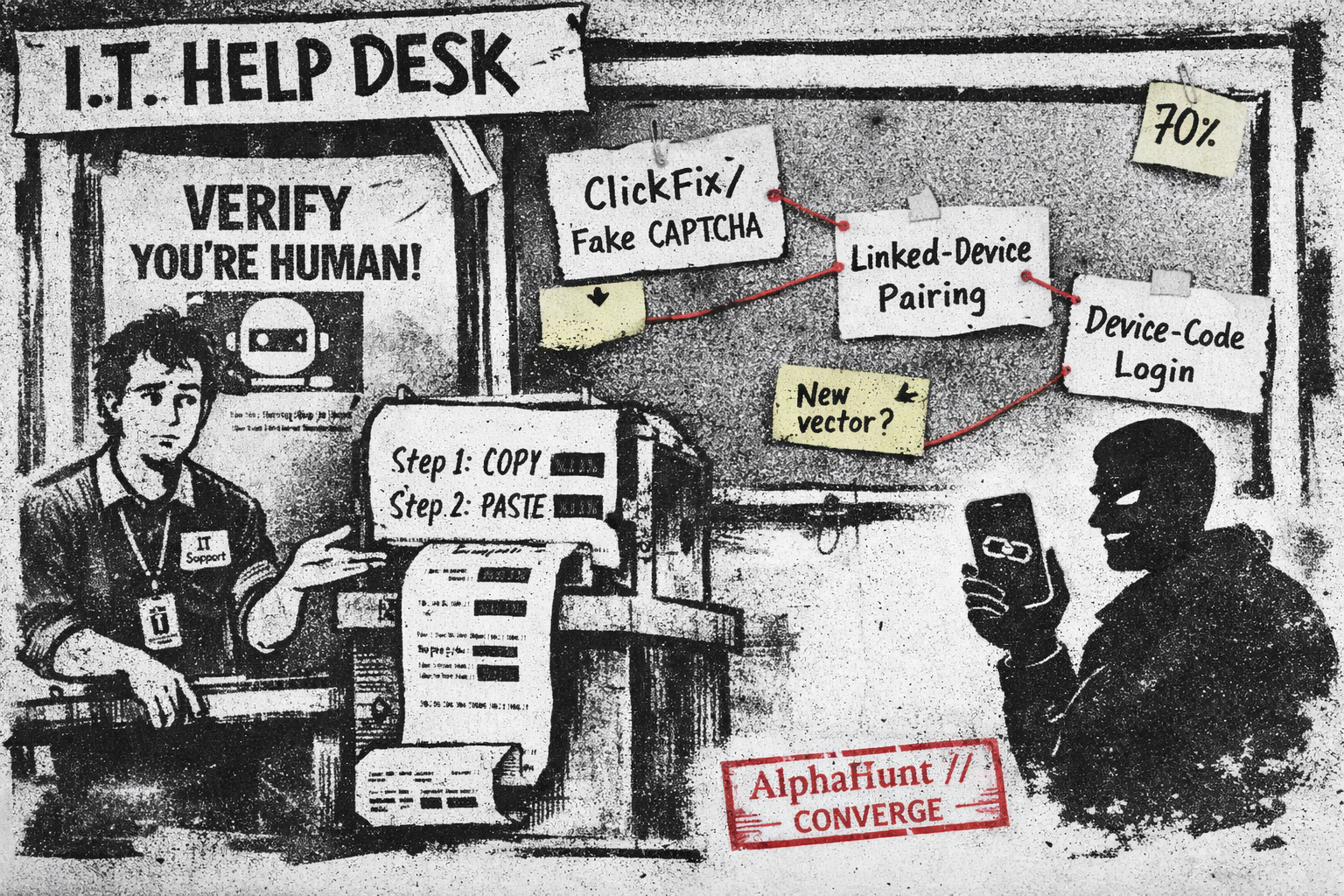
Nothing says ‘secure’ like asking users to paste commands into Run.
Nothing says ‘secure’ like asking users to paste commands into Run.
Vendors are naming slices of the same IIS SEO fraud problem differently. This summary aligns those labels into one unified hunt surface and shows how to separate UAT-8099/WEBJACK from other BadIIS-style activity using concrete host and HTTP fingerprints.
“Normal traffic” is now an attacker costume. 🥸🏠
Residential proxies borrow real home ISP IPs, making sprays/scrapes/SaaS intrusion blend in. Don’t rage-block—use tiered friction (identity+behavior) w/ proxy intel as a risk multiplier.
Ransom is a tactic. Liquidity is the strategy.
Our new forecast asks: will ShinyHunters make more in 2H 2026 by selling SaaS access/data than by getting paid? Signals say yes. 🕵️♂️💸☁️
Your new “AI helper” is basically shadow IT with hands 🤖🧨
Your “AI coworker” isn’t the breach. The OAuth trust event is. 🔥🕵️
Device-code phishing + consent traps = “approve to exfil.” (And yes, AI agents are already being used as the wrapper.)
No malware. Still owned. 🧾🔑💬
Device-code phishing + Teams as the “lobby” + stolen OAuth tokens = API-speed SaaS exfil. If you’re hunting binaries, you’re late.


![[FORECAST] ShinyHunters SaaS Data Theft: Why Non-Ransom Monetization Looks Increasingly Attractive](https://images.squarespace-cdn.com/content/v1/54bd1221e4b05e8a3646d021/1770053581353-COX4JWQFSYW6WFHYQYME/z.png)


