ClickFix to Linked-Device Takeovers: Will Star Blizzard Introduce a New Initial-Access Vector by Oct 2026?
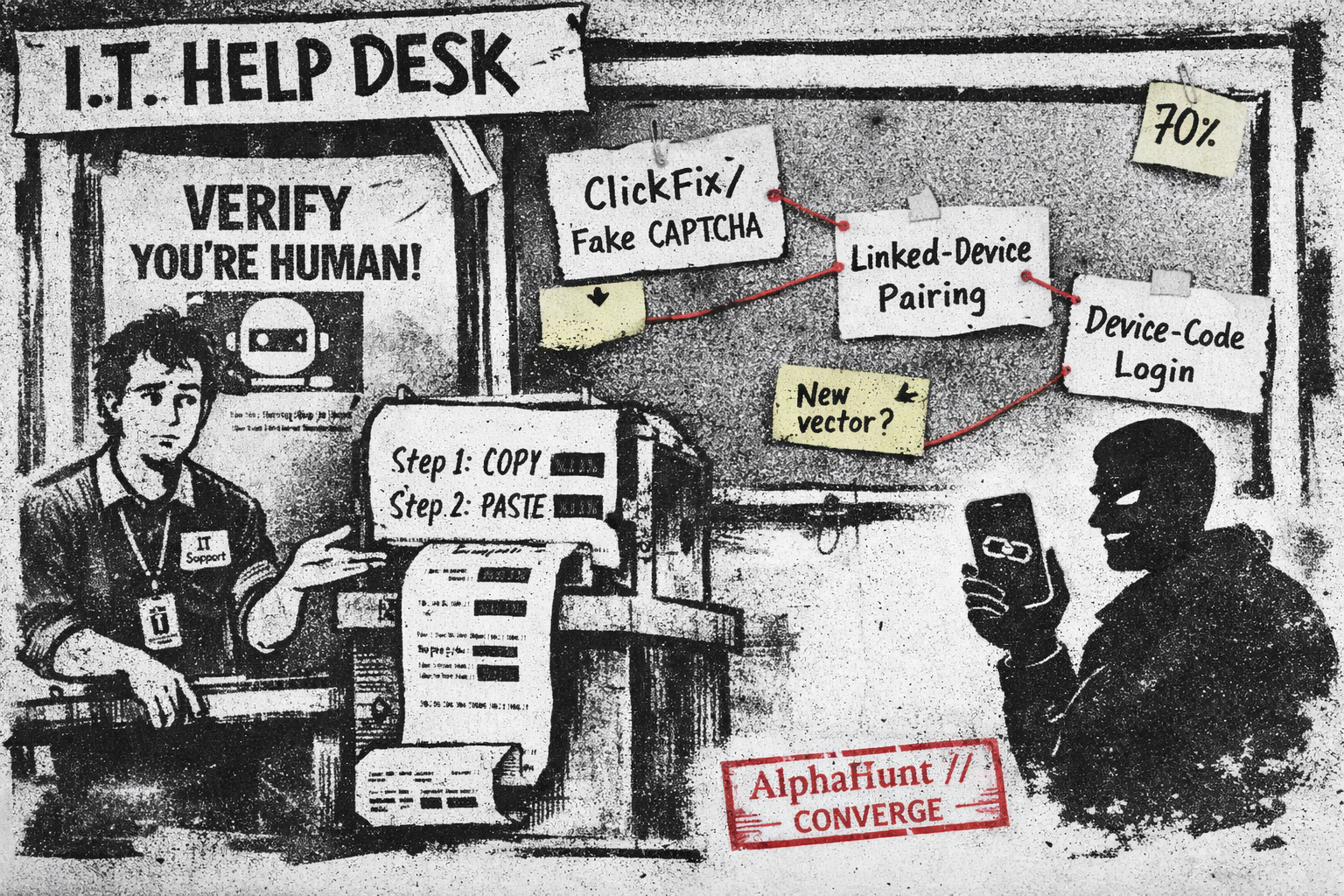
Nothing says ‘secure’ like asking users to paste commands into Run.
Nothing says ‘secure’ like asking users to paste commands into Run.
COLDRIVER went from LOSTKEYS to a full “ROBOT” chain and ClickFix tricks—then started poking linked-device flows. We put 75% on a truly new family or access vector within 12 months.
Russia-linked actors leaned hard on OAuth device codes and RDP phishing from Oct 2024–Aug 2025. Providers pushed back in concert. Here’s what changed, what to watch in your logs, and the quickest moves that buy real risk reduction.
Russian-linked RomCom is abusing a critical WinRAR bug to quietly persist in networks, move laterally, and siphon data over encrypted channels — hitting government, finance, and telecom sectors hard. Patch lag is keeping doors wide open.
DarkWatchMan is a fileless, modular malware family first observed in late 2021 and attributed to the financially motivated Hive0117 group. The malware is primarily delivered via spear-phishing emails containing password-protected archives, targeting Russian critical infrastructure (energy, etc).



